Update for 8th March 2024: More or less an hour after I posted on x.com, the vulnerability no longer exists. It looks like the fireflies.ai team invalidated their Growthbook.io key.
I reached out to the Fireflies.ai security team on the 20th Dec 2023 about an issue I found in their browser extension for their service. I received a standard ZenDesk ticket response, but nothing else after. About a week after that, I contacted them through their report a vulnerability form but did not hear back from them yet again. I looked at HackerOne’s disclose a vulnerability option to report it, but they make things way too restrictive and nebulous for me to even think of working with them. So here I am writing about this piddly little information leakage bug I found.
If you use Fireflies.ai, you know what it is and this post is probably more relevant to you. If not, then I’m not giving them free advertising. Fireflies.ai uses Growthbook.io. Growthbook can best be described as the #1 open source feature flagging and experimentation platform. Their words, not mine. I don’t actually know what it does but from the little I gathered, you can use it to toggle features on and off in your app without re-publishing it and then see how those changes affect user behavior. Yay growth.
This all came about when I was screwing around with my browser DOM because I was trying to read yet another useless article behind a paywall and I saw this one request to cdn.growthbook.io in the developer console’s network tab. The response was JSON and contained enough email addresses and domains for me to abandon my pursuit of finding out why AI will be taking over all our jobs next Thursday. A few minutes of grepping (which is, I guess, a glorified way of saying I hit Ctrl+F and searched for a bunch of shit) and I found the source of the request to be the Fireflies.ai Chrome extension I had installed on my browser. It was calling Growthbook’s SDK end-point to fetch a list of feature flags. My assumption is that the Fireflies.ai dev team uses Growthbook feature flags for all of their web and mobile apps including the extension. Growthbook has some comparison operators that can be used to determine if and when to turn a feature on or off and the team seem to have made extensive use of that feature. Now I don’t know if the Fireflies.ai dev team were told it was a good idea to put emails and domains in Growthbook’s feature flags, which was clearly public and available for all to see, or if it was just a shortcut they took. Basically that’s the vulnerability.
Anyone that knows Fireflies.ai’s client key and the url to fetch feature flags from Growthbook can download well over 400 email addresses and about 240 domain names that are all using Fireflies.ai. If you look through the source code to the chrome extension, then you should be able to find both client key and url. As a matter of fact, you will find the exact url which contains the client key needed to fetch the list of feature flags. Call that url with curl and you will see the emails and domains of the Fireflies.ai users.
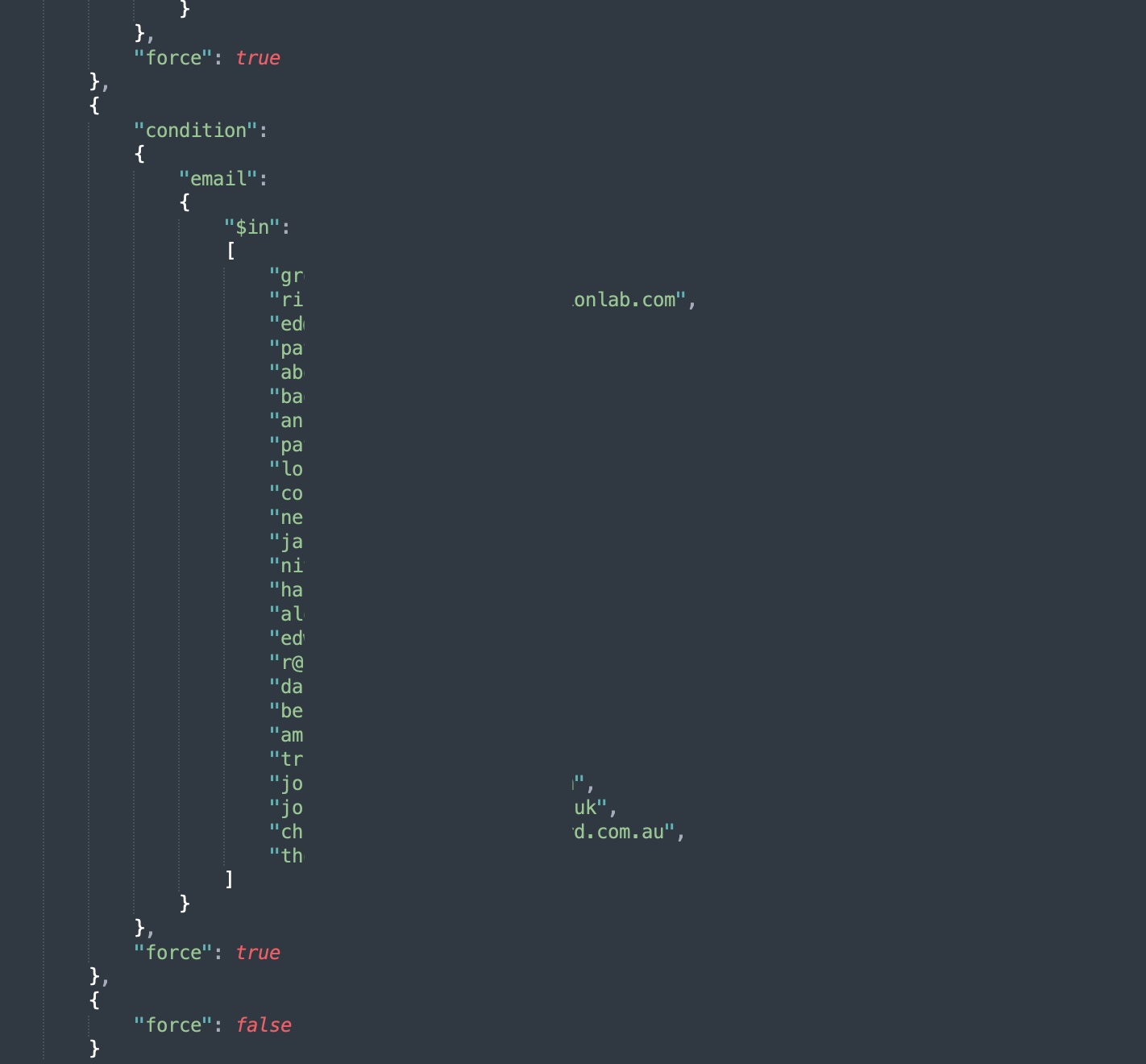
In the screenshot above, you can see the conditional checks being done with the feature flags.
That’s it. That’s the finding.